Quick Contact
Need Help?
Please Feel Free To Contact Us. We Will Get Back To You With 1-2 Business Days.
info@example.com
(888) 123-4567
Download
Company White Paper
1.30 MB
Company Media Kit
1.22 MB
Cyber Security Solutions
Cyber-security, computer security or IT security is the protection of computer systems from theft of or damage to their hardware, software or electronic data, as well as from disruption or misdirection of the services they provide. Cybersecurity includes controlling physical access to system hardware, as well as protecting against harm that may be done via network access, malicious data and code injection. Also, due to malpractice by operators, whether intentional or accidental, IT security personnel are susceptible to being tricked into deviating from secure procedures through various methods of social engineering.

IDENTIFY SECURITY BREACHES
We identify vulnerability weakness in design, implementation, operation or internal control. They include Backdoor cryptosystem, Denial-of-service attacks, Direct-access attacks, Eavesdropping, Spoofing, Tampering, Privilege escalation, Phishing, Click-jacking, Social engineering and Multi-vector, polymorphic attacks.

PROTECT YOUR DATA
Our solutions include Security by design, Security architecture, Security measures, Vulnerability management, Reducing vulnerabilities, Hardware protection mechanisms, Secure operating systems, Secure coding, Capabilities and access control lists, End user security training and Response to breaches.
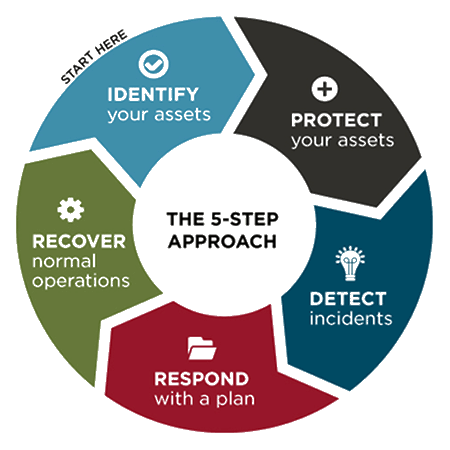
Identify > Protect > Detect > Respond > Recover
Identify
Protect
Detect
Respond
Recover
DATA SECURITY
- Data Loss Prevention.
- Full Disk Encryption.
- File Integrity.
- Database Protection.
NETWORK SECURITY
- Intrusion Prevention Systems (IPS).
- Firewall/Unified Threat Management Systems (UTMs).
- Network Access Control (NAC).
- Advanced Malware Protection (AMP).
- Email, Web & Domain Name Security.
EDGE SECURITY (ENDPOINT SECURITY)
- Mobile Device Security Management (MDSM).
- Industrial Control Systems Solutions (ICS).
- Configuration and Vulnerability Management.
- Endpoint Protection.
- Asset Management.
APPLICATION SECURITY
- Vulnerability Management.
- Mobile Application Management.
SECURITY MANAGEMENT
- Security Intelligence.
- Security Consoles.
